TLS1.2 support available in Unsniff Network Analyzer
We are pleased to announce the availability to TLS 1.2 analysis and decryption in the latest builds of Unsniff Network Analyzer.
The main changes are :
- Change in the way the PRF (Pseudo Random Function) works in TLS1.2
- Addition of SHA256
- Change in the way the IV (Initialization Vector) is derived for block ciphers such as AES-256-CBC
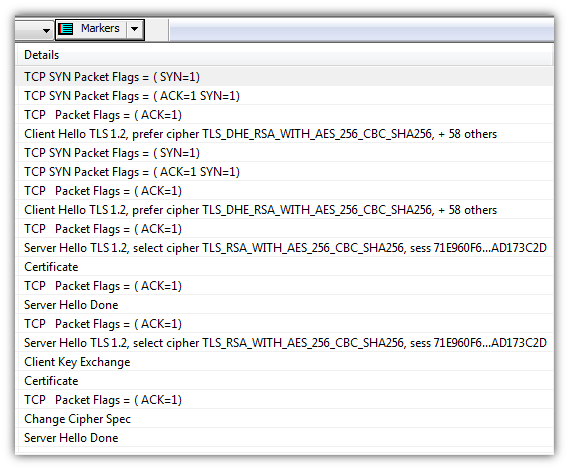
- Currently we support the AES suites like TLS_RSA_WITH_AES_256_CBC_SHA256
- DHE ciphers are also supported by directly entering the master secret
Other changes
- The Session ID is shown differently, we show first and last digits so it is easier for you to search in application logs for the master secret
- A help dialog box is added that helps you convert between PKCS12 – PEM – PCKS8 formats
We will be adding other ciphers such as the AES-GCM mode soon. We encourage users to give feedback about how they are using Unsniff. Specifically we’d like to know the following when working with DHE aided by application logging the master secrets.
- It is extremely tedious to search for SessionID matches against the master secret. How do you log the master secrets ?
- Would you like the ability for Unsniff to automatically match the master secrets with the Session ID ? This could take some work. Is this useful ?
Stay tuned as we announce the next build which will have the AES-GCM support.
Head on over to the Downloads page to get the latest Unsniff Network Analyzer free download.