We observed a very common pattern among users of Unsniff and well as Wireshark. A majority of the time display filters were being used on a combination of the 5-tuples of a TCP or a UDP packet. This was over 90% of the cases. We decided to work on a nifty solution.
A context aware packet filter.
- Right click on any packet to bring up a “Pull out packets” menu with automatic filter choices.
- Select a choice to pull out only matching packets into a new capture file window.
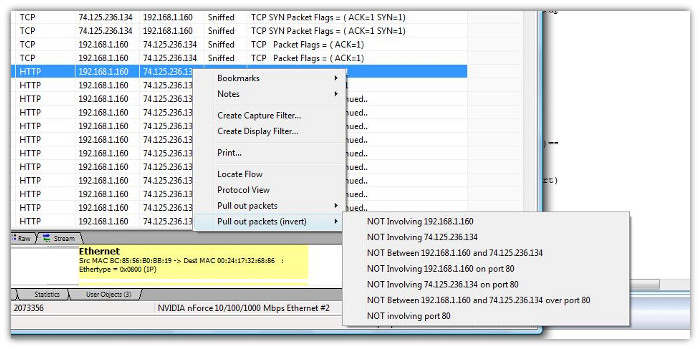
- Unsniff also has “invert” choices. Use them if you want to only select packets NOT matching the selected criteria.
Now, you can zip through capture files effortlessly and narrow down your analysis data.
Start saving time and energy while perusing packet captures. Download the latest version of Unsniff Network Analyzer
Some screenshots follow.
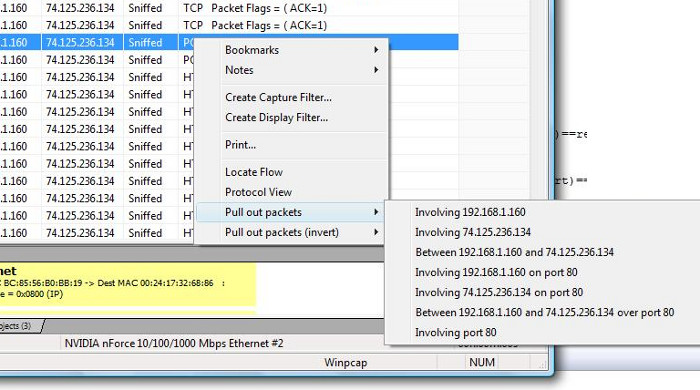
and the inverted filter
More exciting news about Unsniff Network Analyzer coming soon.