Cisco released three security advisories for its IOS platform two days back. See Tech Lounge, Tao Security, The Register, for more coverage. Note: These affect almost all 12.0, 12.1, 12.2 of IOS routers.
- Malformed TCP Packets (denial of service). Specially crafted TCP packets can leak small amount of memory, which over time can result in a DoS.
- IPv6 Routing Header (crashes IOS !). Only if IPv6 has been enabled, this is a bug when source routing is enabled.
- *serious* Â IP Option vulnerability (can execute arbitrary code). A specially crafted IP options packet can compromise the router.
All three are triggered by a malformed packet. These packets can contain spoofed addresses, so a traditional ACL may not be effective.
Of the three, the third is obviously the most serious. Security watchers are reporting that there is a lot of interest in underground forums about how to exploit the third one.
“These are serious issues and patches need to be applied as soon as possible,” said Gunter Ollmann, director of security strategy for IBM Internet Security Systems. “From our monitoring of underground channels there are a lot of people interested in these and actively working on exploits.”
So what is an IP option ?
For those who are not familiar with it, here is a sample IP option viewed using Unsniff Network Analyzer. IP options are extensions to the standard IPv4 header to implement some additional functionality.
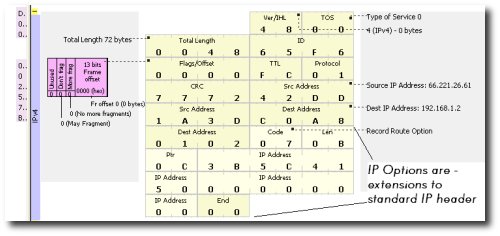
What you see in the picture is a “Record route option”. You can append other options after it, and close with an “End” option (Identified by code 00).
[tags] cisco , security, ip options, unsniff [/tags]
1 thought on “IP Option Vulnerability in Cisco IOS – Update now !”
Comments are closed.