In Part-1, we used the Unsniff Scripting API to read a PCAP file and print the Certificate Chain for all HTTPS connections in it.
What if you did not have a PCAP (Packet Capture) file ?
In the real world, getting a sufficiently narrow PCAP file is the problem. If you have an NSM system with a strong API – you can conjure up whatever analysis you want on previously captured data. Using the Trisul API (a.k.a Trisul Remote Protocol or TRP) you can write Ruby scripts to :
- securely connect to a Trisul Probe
- search for various types of data (traffic stats, flows, alerts, URLs, DNS, and packets)
- pull out required PCAPs for further deep processing by Unsniff or Wireshark
Task for Part 2
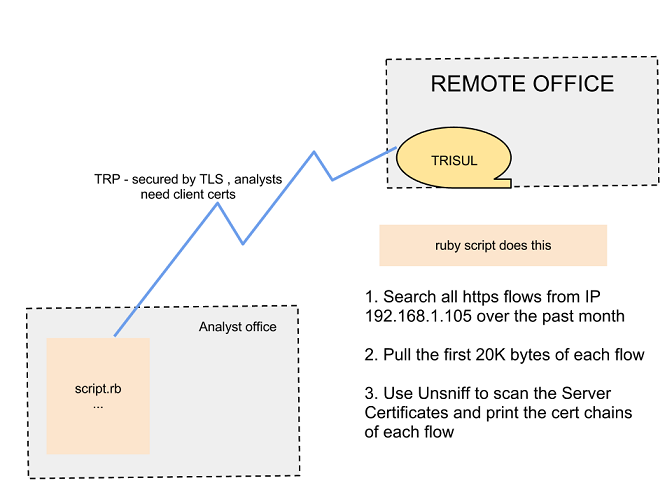
We have a TRP Server running on demo2-dot-trisul-dot-org – your task is to connect to this server, search for all HTTPS activity from a suspicious host 192.168.1.105 over the past 1 month and print out the certificate chain of each connection. This will help you cut through several gigabytes of packets.
The setup for TRP
Try it out first
Before we explain the code, lets gratify ourselves by running the sample code and getting some output.
- Install Ruby and the trisulrp gem (see the tutorial for help)
- Install Unsniff Network Analyzer (free) from the downloads page. You need this to do the deep analysis. Sorry this is a Windows MSI. If you are running Linux just comment out the print_cert_stack function.
- Download the csx.rb script from the samples page
- Download the demo client cert and key from and place them in the same directory
Note: You dont need to install Trisul or the Web Interface. We already have a probe running on demo2trisulorg. You are just setting up a script client environment.
Run as below (password for the private key file is ‘client’ )
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
C:\Users\Vivek\Documents\devbo\us\certxtrp>ruby csx.rb demo2.trisul.org 12001 192.168.1.105 https Enter PEM pass phrase: Certificate chain for 65.55.184.155 to 192.168.1.105 www.update.microsoft.com (Microsoft) Microsoft Secure Server Authority () Microsoft Secure Server Authority () Microsoft Internet Authority () Microsoft Internet Authority () GTE CyberTrust Global Root (GTE Corporation) Certificate chain for 65.55.184.27 to 192.168.1.105 www.update.microsoft.com (Microsoft) Microsoft Secure Server Authority () Microsoft Secure Server Authority () Microsoft Internet Authority () Microsoft Internet Authority () GTE CyberTrust Global Root (GTE Corporation) Certificate chain for 198.232.168.144 to 192.168.1.105 registration2.services.openoffice.org (Sun Microsystems, Inc) Sun Microsystems Inc SSL CA (Sun Microsystems Inc) Sun Microsystems Inc SSL CA (Sun Microsystems Inc) (VeriSign, Inc.) (VeriSign, Inc.) (VeriSign, Inc.) |
The csx.rb code
The code is quite straightforward.
Step 1. We connect to TRP and retrieve 20 HTTPS flows for IP 192.168.1.105 for the entire time interval available. The message used here is KeySessionActivity (give me all flows by IP and/or Port)
|
1 2 3 4 5 6 |
# send request for sessions for key req = TrisulRP::Protocol.mk_request(TRP::Message::Command::KEY_SESS_ACTIVITY_REQUEST, :key => target_ip , :key2 => target_port , :maxitems => 20 , :time_interval => mk_time_interval(tmarr)) |
Step 2 : For each flow in the response, pull the packets out of Trisul. The message used here is FiltereredDatagramsRequest for each flow. Note we have capped the :max_bytes at 20,000. We use a trick here, we only retrieve the first 20K bytes of each flow because the Server Certificate is usually exchanged at the very beginning of a SSL session. This dramatically reduces the data transferred.
|
1 2 3 4 5 6 |
# get response and print session details TrisulRP::Protocol.get_response(conn,req) do |resp| resp.sessions.each do |sess| get_packets = TrisulRP::Protocol.mk_request(TRP::Message::Command::FILTERED_DATAGRAMS_REQUEST, :max_bytes => 20000, :session => ... |
The full code is available as csx.rb from the TRP Samples Page.
Have fun !
—
We just released Trisul 2.4. The major new feature in it is the API (Trisul Remote Protocol). Download it and let it watch your network. You never know when you may need its data.